Shalom Everyone 👋,
Welcome to Day 5 of our Cloud Day Series. I'm so happy you're here with me! Today, we'll talk about AWS VPC and how it helps with cloud networking. If you're new here, I'm Ashok, a recent graduate with a passion for technology and development. On Hashnode, I pen down my insights on DevOps within the AWS Cloud and discuss nuances of React and React Native development.
Now that you know a bit more about me, let's embark on today's Cloud adventure 🚀...
What is a Network
Well, first see what exactly a network is...
A network is like a digital conversation among devices. Think of it as computers, phones, and any other gadgets connected together. They chat, share data, and transfer info to one another. It's all about communication and sharing in the digital world.
How Network Communication Works
Network communication is a vast and intricate field, but let's break it down. Imagine texting your favorite person. While it feels immediate, there's a complex dance happening behind the scenes. Your message goes through various layers of the network (akin to the OSI or TCP/IP models). It gets broken down into 'packets' of data. As these packets journey across the network, they're routed through various devices, undergo error-checking, might be encrypted for security, and then they're directed to their destination based on addressing protocols. Once they arrive, they're reassembled, so your friend sees the message you sent.
What is VPC in AWS ...?
AWS VPC, or 'Virtual Private Cloud', is a service offered by Amazon Web Services. It allows you to create isolated space in AWS Cloud where you can run your resources in a network you define. In simpler terms, think of it like creating your own private town on a vast land called AWS. In this personal town (VPC), you have control over the layout, who comes in, who goes out, and how the houses (servers) communicate. It's a way to have a private, secure space in the cloud to set up and manage your digital resources.

Regions
Amazon Web Services (AWS) regions are geographically distinct areas around the world where all your infrastructure is located. Each region has multiple Availability Zones. Availability Zones are isolated from each other to protect against service disruptions. You can choose to deploy your applications and data across multiple AZs to achieve high availability and fault tolerance.
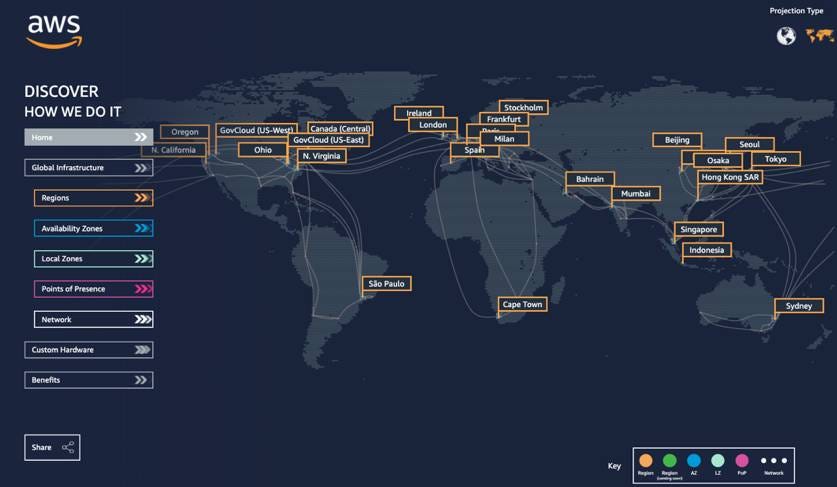
Check AWS Regions over the Globe
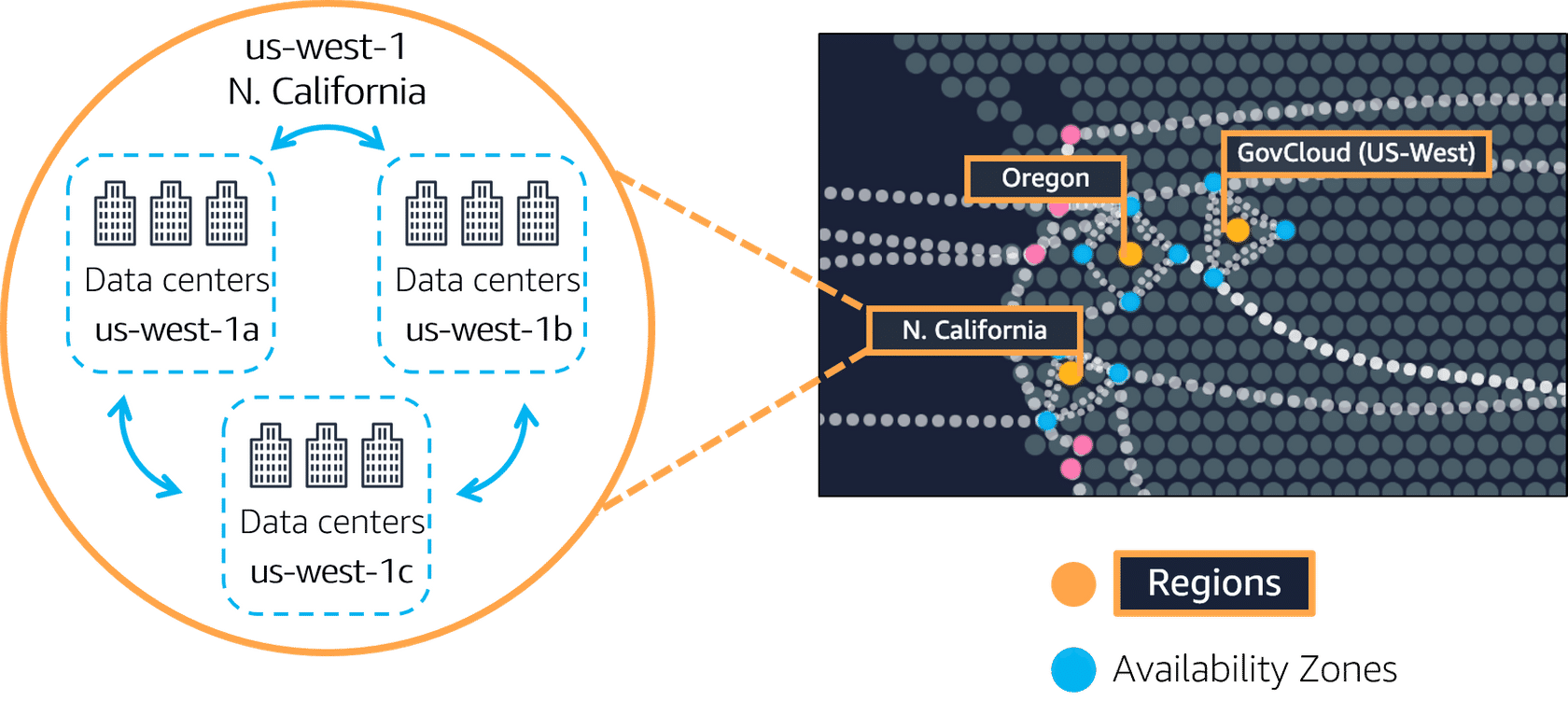
Availability Zones
Availability Zones (AZs) are simply data centers equipped with power, cooling, and networking to operate your services in the cloud. Having multiple Availability Zones is like having multiple power backup systems for your house. if one fails, the other can take over. By spreading your resources across different AZs, AWS ensures that if there's an issue with one AZ, your application can still run smoothly using the resources from another AZ.
CIDR
CIDR, which stands for "Classless Inter-Domain Routing," is a technique employed to allocate IP addresses and direct IP packets on the internet. When setting up a VPC, as we discussed earlier, you need to define a range of IP addresses using CIDR notation. This range determines how many private IPs you can use within your VPC.
IPs Allocation
For example, you created your VPC in the AWS cloud. Setting up a Virtual Private Cloud (VPC) means you'll be diving into the realm of IP addresses. The first step is to select an IP range using CIDR notation, like 10.0.0.0/16. This "/" notation is like a shorthand that defines how big your address space is. To decipher how many IPs you have in total,
there's a formula:
Total IPs=2 (32−CIDR prefix).
So, with a /16, you're looking at a whopping 65,536 IPs! However, not all these are up for grabs. The first and last IPs in this range are reserved, leaving you with 65,534 usable IPs. With that vast pool, you're set to segment them across different parts of your VPC, be it different subnets or specific services. In essence, understanding IP allocation for your VPC is about choosing an address range and then determining how many of those addresses are usable for your cloud setup.
Public and Private IPs

Public and private IP addresses are two different types of IP addresses that are used to identify devices on the internet. Public IP addresses are unique addresses that are assigned to devices by internet service providers (ISPs) and are used to route traffic over the public internet. Private IP addresses, on the other hand, are used to identify devices on private networks, such as home networks and business networks. Private IP addresses are not routable over the public internet, but they can be used to communicate with other devices on the same private network.
Subnets
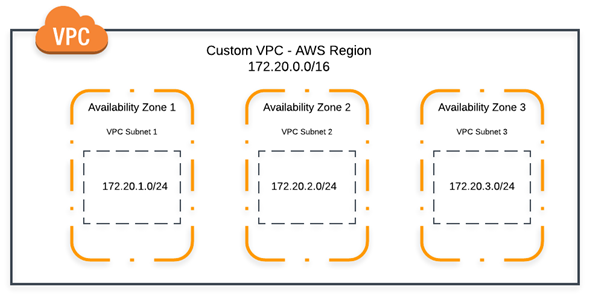
Subnets are a way to divide a large network into smaller groups, more manageable networks. Subnets are typically created by dividing a network's IP address range into smaller blocks. Each subnet is assigned a unique CIDR block, which is a subnet mask and a network address. The subnet mask determines how many bits of the IP address are used to identify the subnet and how many bits are used to identify the host. The network address is the first IP address in the subnet.
NACL
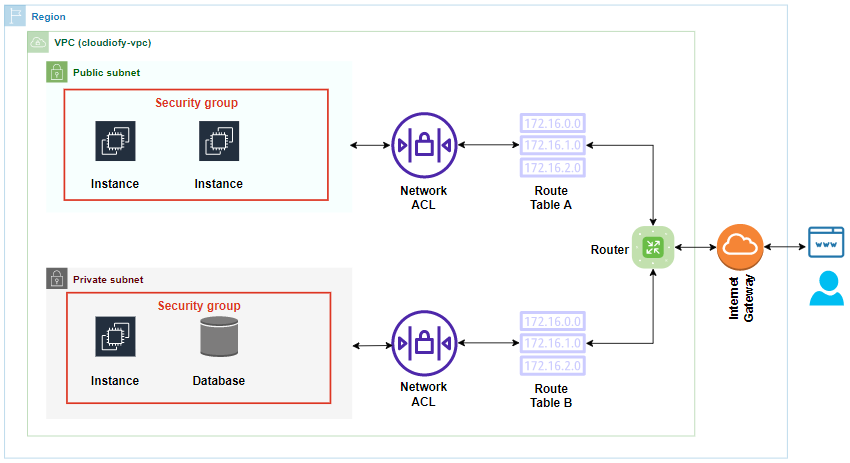
A Network Access Control List (NACL) is a firewall that can be used to control incoming and outgoing traffic on a subnet. NACLs allow you to specify which traffic is allowed and which traffic is denied. NACLs can be used to protect subnets from unauthorized access, to prevent denial-of-service attacks, and to enforce security policies.
NACLs can be applied to individual subnets or to groups of subnets and can also be applied to specific interfaces on a subnet. For example, you could create an NACL that allows all incoming traffic to a web server subnet, but only allows outgoing traffic to the internet.
NACLs are an important part of network security and can help to protect your subnets from unauthorized access. NACLs can also be used to enforce security policies and to prevent denial-of-service attacks.
Security Groups
A security group is a logical firewall that controls inbound and outbound network traffic at the instance level. Security groups act at the instance level, not the subnet level each instance can belong to multiple security groups, and each security group can be applied to multiple instances. This allows you to define fine-grained access control rules for your instances.
Gateways
Gateways are network devices that allow traffic to pass between different networks. Gateways can be used to connect two networks that use different protocols, such as an IP network and an Ethernet network. Gateways can also be used to connect two networks that use different IP address ranges, such as a private network and a public network.
Gateways are essential for connecting VPCs to the public internet and to on-premises networks. Without gateways, traffic would not be able to flow between these different networks.
Conclusion
Thank you for joining with me on this Blog series. I hope you learned these important networking concepts. If you found it valuable, please show some love with a ❤️ and share your thoughts 🤗.
See you in our next Cloud Day Series... Farewell for now! 👋
Let's connect on ...